Banking websites and XSS: it's time for CSP
DongIT once again finds vulnerabilities in banking websites: a year after the event
In January 2015, DongIT proved that 10 Dutch banking websites were vulnerable to cross-site-scripting (XSS) on their main domain. In August 2016, DongIT executed new security research approximately a year later.
The research aims to determine whether banks are now using an extra security layer, named Content Security Policy, to prevent repetition.
Result of the research: New XSS vulnerabilities were found on the main domains of ABN Amro, Triodos, and SNS bank.
Download the full article here (only available in Dutch): Banking websites and XSS: time for CSP v1.0
Why are these findings significant?
The impact of an XSS vulnerability is most critical on the main domain (i.e., www.abnamro.nl) or the banking domain of the bank because this is familiar to the visitor, and banking transactions occur here. The web address will appear unchanged in the address bar, including the Trustmark lock – despite the attack. The trustworthy character can trick the visitor into believing they are logging in with their DigiD-account (a Dutch authentication system offered by the government). At the same time, data is sent to the attacker in the background.
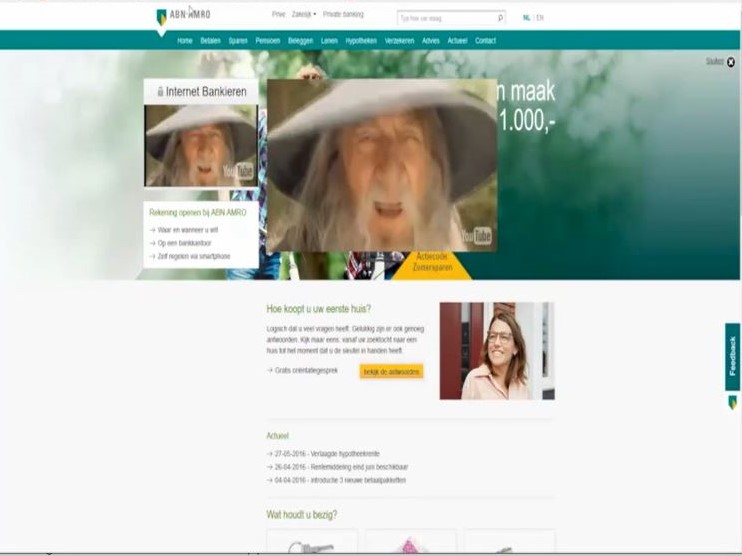
Following is an example of an XSS attack on the primary domain of ABN Amro. A form is injected into the website, which cannot be distinguished from a simple form. It appears to be possible to log in with DigiD. In general, the trustworthiness of the domain www.abnamro.nl will not make most visitors suspicious of this. Passwords are sent to the attacker in the background.
Another example is the following simple and remarkable manipulation of the website, showing the attacker has complete control over the banking website's browser.
The video of the previous research (2015) is shown below. This video shows ten banking websites doing the "Harlem Shake" on its root domain.