Vulnerable software versions of municipal web systems mapped
Vulnerabilities in Dutch municipalities software mapped by DongIT
In February 2013, DongIT mapped as many software versions of web systems of all Dutch municipalities as possible using a script linked to several open-source tools. The vulnerabilities and corresponding impact classifications were mapped from all detected software versions.
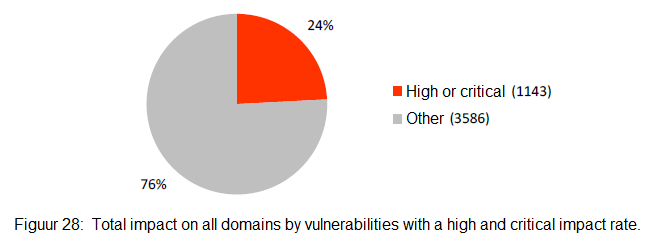
Analyses of up-to-date or non-vulnerable systems, as opposed to systems with high and critical impact classifications, conclude that after all fuss since Lektober in 2011, much old software is still in use. These critical/high-impact vulnerabilities affect both large and small municipalities. With a few software packages, such as Drupal, Joomla, PHPMyAdmin, Apache, and PHP, DongIT was found vulnerable primarily to software versions. Vulnerabilities can exploit 24% of all detected software used by municipalities with a high critical impact rate. Malevolent users can easily misuse the software used on these systems.
Research shows that current efforts to secure municipal systems did not proven effective. People should be continuously aware of which systems are present and publicly accessible. Systems that do not have to be publicly accessible should be isolated and secured. The focus should be on keeping the systems up to date. The document "ICT-Guidelines for Web applications" from the National Cyber Security Center defines how an update process should be executed. The strategy's effectiveness can be examined by performing similar research periodically.
You can download the full report and an article written by InGovernment (both in Dutch) below: